We are currently seeing some issues sending TLS encrypted mails to Outlook.com hosted email addresses.
This appears to only be affecting some of the Outlook.com hosted server ip addresses intermittently
213.199.154.87 / mail-db34087.inbound.protection.outlook.com
213.199.154.23 / mail-am14023.inbound.protection.outlook.com
If messages fail to be delivered, you will receive a bounce message similar to the following:
TLS connect failed: timed out; connected to 213.199.154.87.
I’m not going to try again; this message has been in the queue too long.
In the interim we have disabled TLS encryption to the affected addresses.
We are currently unsure if this is a Microsoft issue, or a China Firewall Issue, so this may or may not resolve the issue.
We will update this post when we have further information.
16
SSL Updates
The SSL certificate for the all servers have been updated to use a wildcard certificate.
We *finally* changed over to use a wildcard cert, as pricing has come down enough to not warrant having separate certificates per server.
Our new wildcard certificate is valid until 2019.
What does this mean for you?
The bad news
Really old browsers won’t be able to open our site
If you are an XP user running IE6, you won’t be able to load our encrypted sites anymore. We strongly suggest you upgrade though if you fall into that category!
Same goes for those running Android 2.x (which is equally ancient in computer terms).
The good news
Email is now encrypted point to point using AES256 SHA encryption where possible, and webmail is SHA256 encrypted from server to your browser.
Mail servers that support it (i.e. all of ours, plus the major providers like Google, Yahoo etc, will send encrypted mail to our servers).
Mail Headers will include things like the below if encryption is supported –
Received: from usa4.computersolutions.cn (162.210.36.26) by mail.computersolutions.cn with AES256-SHA encrypted SMTP;
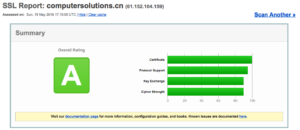
Lastly – our new cert gets us a test rating of A at the SSL Labs site.
https://www.ssllabs.com/ssltest/analyze.html?d=computersolutions.cn&latest
One of our clients sent us an email this morning letting us know that they couldn’t send an email to a client.
They forwarded the bounce message to us (below)
12.149.35.75 does not like recipient.
Remote host said: 554 Service unavailable; Client host [usa.computersolutions.cn] blocked using Barracuda Reputation; http://bbl.barracudacentral.com/q.cgi?ip=72.51.39.20
Giving up on 12.149.35.75.
Simple enough – we’re getting blocked by Barracuda Reputation, so off I go to the link to see why.
Sorry, your email was blocked
We are sorry you have reached this page because an email was blocked based on its originating IP address having a “poor” reputation. The “poor” reputation may have been caused by one of the following reasons:
* Your email server contains a virus and has been sending out spam.
* Your email server may be misconfigured.
* Your PC may be infected with a virus or botnet software program.
* Someone in your organization may have a PC infected with a virus or botnet program.
* You may be utilizing a dynamic IP address which was previously utilized by a known spammer.
* Your marketing department may be sending out bulk emails that do not comply with the CAN-SPAM Act.
* You may have an insecure wireless network which is allowing unknown users to use your network to send spam.
* In some rare cases, your recipient’s Barracuda Spam Firewall may be misconfigured.
A quick check of our ip space over at a more legitimate place shows we’re fine – http://www.senderbase.org/senderbase_queries/detailip?search_string=72.51.39.20
I double check with a rbl lookup over here – http://www.mxtoolbox.com/blacklists.aspx, nope, we’re clean as a whistle.
However, on the same page, they have an big button helpfully letting us know that:
Many Barracuda Spam & Virus Firewalls are configured, as a policy, to automatically deliver email that comes from sources that are properly registered at EmailReg.org.
Ok, so follow the link through to EmailReg.org, and sign up.
Looks good until we get to the – a $20 fee will be charged per domain per year.
Hmm, so email will possibly be blocked by Barracuda unless I pay them $20 a year.
Sounds like Blackmail to me.
I also note that although EmailReg.org appears to be a separate entity, it is in fact owned by Barracuda. So a neutral third party blocking service just so happens to be owned by the people doing the blocking. If thats not a conflict of interest, I don’t know what is!
This is actually illegal in some countries, although apparently, not the USA.
It also doesn’t stop actual spammers coughing up money, and getting greenlisted.
Seems the rest of the net agrees with us on this one.
Quote from Mike E. that pretty much sums it up: I feel compelled to add this. If I’m paying Barracuda for a appliance to filter out spam and they in turn are being paid by spammers to allow their messages through my spam firewall, how is that different than an antivirus company taking money from somone that write viruses to have their product not detect a virus? None. It’s slimy.
So, in future when clients are unable to send mail to people using Barracuda firewall devices, I’ll be able to point them to this post, and let them know the situation.
We don’t like spam either, and work hard to avoid clients misusing our services.
However, we don’t blackmail senders into paying us money to accept their mail.
For a rundown on legitimate practices, read this:
http://en.wikipedia.org/wiki/Anti-spam_techniques_(e-mail)
Further References/Complaints:
http://www.nabble.com/zen.spamhaus.org-td22805806.html
http://www.debian-administration.org/users/simonw/weblog/295
http://zacharyozer.blogspot.com/2008/10/worst-engineers-ever.html
http://andrew.triumf.ca/barracuda-problems.html
http://community.spiceworks.com/topic/32502
http://steve.heyvan.com/2008/11/06/technology-reviews/barracudacentral-another-blacklist-black-hole/
http://ithelp.ithome.com.tw/question/10013491?tab=opinion (Trad Chinese)
http://www.linux.com/feature/155880
Archives
- November 2024
- November 2019
- October 2019
- August 2019
- April 2019
- February 2017
- September 2016
- June 2016
- May 2016
- September 2015
- August 2015
- June 2015
- April 2015
- December 2014
- October 2014
- September 2014
- July 2014
- June 2014
- April 2014
- October 2013
- July 2013
- May 2013
- April 2013
- March 2013
- January 2013
- December 2012
- October 2012
- August 2012
- July 2012
- June 2012
- May 2012
- April 2012
- March 2012
- December 2011
- November 2011
- October 2011
- September 2011
- July 2011
- May 2011
- April 2011
- March 2011
- February 2011
- January 2011
- December 2010
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
- May 2010
- April 2010
- March 2010
- February 2010
- January 2010
- December 2009
- November 2009
- October 2009
- May 2009
- April 2009
- March 2009
- February 2009
- January 2009
- December 2008
- November 2008
- October 2008
- September 2008
Categories
- Apple
- Arcade Machines
- Badges
- BMW
- China Related
- Cool Hunting
- Exploits
- Firmware
- Food
- General Talk
- government
- IP Cam
- iPhone
- Lasers
- legislation
- MODx
- MySQL
- notice
- qmail
- requirements
- Reviews
- Service Issues
- Tao Bao
- Technical Mumbo Jumbo
- Things that will get me censored
- Travel
- Uncategorized
- Useful Info


