Yet another SSL vulnerability has hit the news – the Poodle SSLv3 vulnerability.
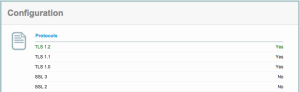
Our servers are already patched against this (we’ve disabled SSLv2 and SSLv3 functionality, and use TLS).
You can check this on the 3rd party site here –
https://www.ssllabs.com/ssltest/analyze.html?d=mail.computersolutions.cn&s=211.144.68.16
Unfortunately this now means that Windows XP and IE6 are no longer supported.
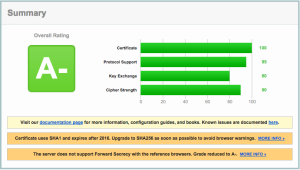
Our rating from the SSLLabs checker is below.
Note that the A- rating is due to our certificate, not our security!
(We can only update that in 2016 when it comes up for renewal).
10
Heartbleed vulnerability
Those of you who follow tech news may have heard about the HeartBleed vulnerability.
This is a rather large bug in SSL libraries in common use that allows an attacker to get unsolicited data from an affected server. Typically this data contains user / password details for user accounts, or secret keys used by servers to encrypt data over SSL.
Once the exploit was released, we immediately tested our own servers to see if we were vulnerable. We use an older non-affected version of SSL, so none of our services are/were affected.
Unfortunately a lot of larger commercial services were affected.
Yahoo in particular was slow to resolve the issue, and I would assume that any users passwords are compromised.
We ourselves saw user/passwords ourselves when we tested the vulnerability checker against Yahoo..
We advise you to change your passwords, especially if the same password was used other sites, as you can safely assume that passwords on other services are compromised.
I also strongly recommend this action for any users of online banking.
There is a list of affected servers here –
https://github.com/musalbas/heartbleed-masstest/blob/master/top1000.txt
Further information about this vulnerability is available here –
http://heartbleed.com/
11
Some remote exploit analysis
Foreword – Note that none of our servers are vulnerable to remote inclusion attacks.
For the most part, most of the exploits I covered in yesterdays post are common garden php vulnerability scans.
Some of them are more interesting though, although more for being encrypted, than anything else.
If I take an example from our log files:
Read more »
Archives
- November 2024
- November 2019
- October 2019
- August 2019
- April 2019
- February 2017
- September 2016
- June 2016
- May 2016
- September 2015
- August 2015
- June 2015
- April 2015
- December 2014
- October 2014
- September 2014
- July 2014
- June 2014
- April 2014
- October 2013
- July 2013
- May 2013
- April 2013
- March 2013
- January 2013
- December 2012
- October 2012
- August 2012
- July 2012
- June 2012
- May 2012
- April 2012
- March 2012
- December 2011
- November 2011
- October 2011
- September 2011
- July 2011
- May 2011
- April 2011
- March 2011
- February 2011
- January 2011
- December 2010
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
- May 2010
- April 2010
- March 2010
- February 2010
- January 2010
- December 2009
- November 2009
- October 2009
- May 2009
- April 2009
- March 2009
- February 2009
- January 2009
- December 2008
- November 2008
- October 2008
- September 2008
Categories
- Apple
- Arcade Machines
- Badges
- BMW
- China Related
- Cool Hunting
- Exploits
- Firmware
- Food
- General Talk
- government
- IP Cam
- iPhone
- Lasers
- legislation
- MODx
- MySQL
- notice
- qmail
- requirements
- Reviews
- Service Issues
- Tao Bao
- Technical Mumbo Jumbo
- Things that will get me censored
- Travel
- Uncategorized
- Useful Info