As one of the main contention points people have with mail service is either the amount of spam they receive, or the amount of legitimate email we block, we’ve decided to put the solution in your hands.
We’ve added user access to the blocking implementation we use at Computer Solutions.
For a quite rerun on this our incoming mail rules are as follows:
- Sending Server has a valid Reverse DNS Entry
- Sending Server conforms to mail RFC’s
- Sending Server is not listed in any of the following Antispam Service Lists zen.spamhaus.org cblplus.anti-spam.org.cn cdl.anti-spam.org.cn bl.spamcop.net dnsbl.njabl.org
- Mail does not contain a virus, malware or similar content.
- Mail is addressed to a valid sender.
- Recipients mailbox is not full.
We’re giving you access to do what you want with regards to incoming spam blocks.
If you decide that our heinous blocking of senders who’s servers are _definitely_ listed in spam listings is not to your taste, then you can change that.
If you want to whitelist any incoming mail you can do the following:
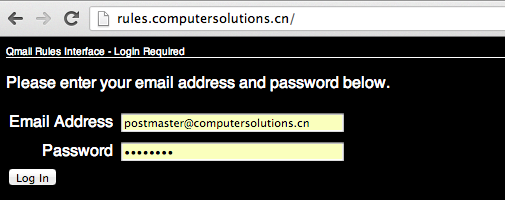
1) Login as the postmaster account for your domain at http://rules.computersolutions.cn (in the example below, I’m editing my own account, you’ll need to use YOUR postmaster@yourdomain.com / password!)
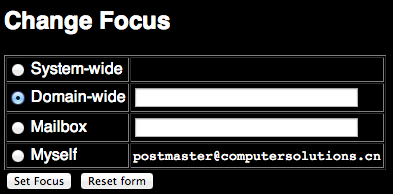
2) Select Domain Wide Focus
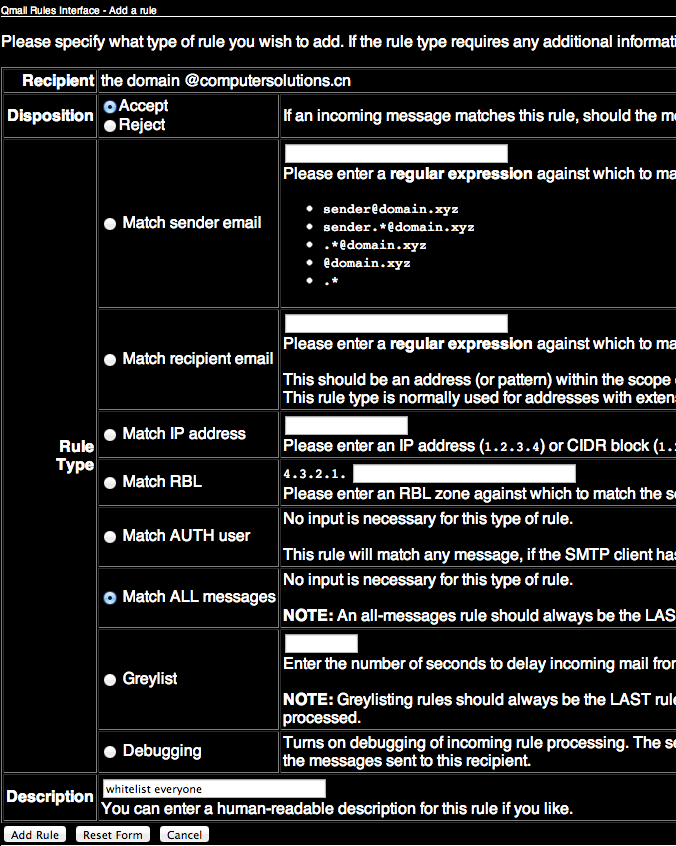
3) Click Add a domain specific rule (this will apply to all messages received for your domain – i.e. anything @yourdomainname.com)
4) Setup appropriate rules (there are a number of options – in the example below I’m whitelisting all incoming mail).
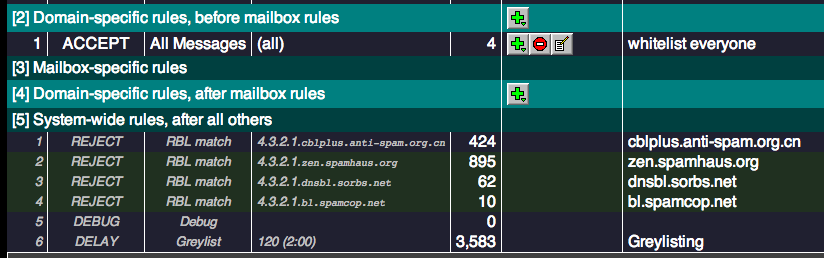
5) Note that the System rules below are now greyed out (assuming you whitelisted as per example above).
Thats because they no longer apply!
In future we will be pushing clients to use this interface for their unblocking / blocking requirements, so that the needs of the few outvote the needs of the many, and your incoming email can go where no wo/man has gone before.
Lawrence.
As we’re a pro-active sort of ISP, we often take a look at ways to improve things for clients under the hood.
One of those improvements, was our recent DMARC implementation for our mail servers.
DMARC is a newish standard which adds to our existing SPF setup, by allowing us to publish methods that tell other providers how mail from us should be processed. It also allows us to receive reports from other providers as to how they’re processing our mail.
20
Spam from Live.com
We’re seeing a huge recurrence of spam thats been getting through our spam filters., all coming from @live.com addresses.
I hadn’t seen any personally until one of our clients brought up the fact that she was receiving 20-30 sex related spam a day, all coming from Random name @live.com addresses.
A check of the logs showed that we’ve received at least 100,000 of these spam mails over the last month that have gotten through to our users.
This is something I’d obviously like to remedy. Not receiving, processing, or storing that much spam free’s up the servers for other things.
As the number of valid addresses using @live.com accounts appears to be minimal (I could only see a handful of legitimate users sending from that domain), I have taken the decision to block any email from the @live.com domain until Microsoft can resolve their spam issues.
If you do have clients using @live.com addresses, you will be able to send email to them, but not receive from them.
We apologize for the inconvenience, but unfortunately there is no other solution that easily mitigates the issue, other than completely blocking them.
For a more technical explanation of whats happening, read below:
Read more »
One of our clients sent us an email this morning letting us know that they couldn’t send an email to a client.
They forwarded the bounce message to us (below)
12.149.35.75 does not like recipient.
Remote host said: 554 Service unavailable; Client host [usa.computersolutions.cn] blocked using Barracuda Reputation; http://bbl.barracudacentral.com/q.cgi?ip=72.51.39.20
Giving up on 12.149.35.75.
Simple enough – we’re getting blocked by Barracuda Reputation, so off I go to the link to see why.
Sorry, your email was blocked
We are sorry you have reached this page because an email was blocked based on its originating IP address having a “poor” reputation. The “poor” reputation may have been caused by one of the following reasons:
* Your email server contains a virus and has been sending out spam.
* Your email server may be misconfigured.
* Your PC may be infected with a virus or botnet software program.
* Someone in your organization may have a PC infected with a virus or botnet program.
* You may be utilizing a dynamic IP address which was previously utilized by a known spammer.
* Your marketing department may be sending out bulk emails that do not comply with the CAN-SPAM Act.
* You may have an insecure wireless network which is allowing unknown users to use your network to send spam.
* In some rare cases, your recipient’s Barracuda Spam Firewall may be misconfigured.
A quick check of our ip space over at a more legitimate place shows we’re fine – http://www.senderbase.org/senderbase_queries/detailip?search_string=72.51.39.20
I double check with a rbl lookup over here – http://www.mxtoolbox.com/blacklists.aspx, nope, we’re clean as a whistle.
However, on the same page, they have an big button helpfully letting us know that:
Many Barracuda Spam & Virus Firewalls are configured, as a policy, to automatically deliver email that comes from sources that are properly registered at EmailReg.org.
Ok, so follow the link through to EmailReg.org, and sign up.
Looks good until we get to the – a $20 fee will be charged per domain per year.
Hmm, so email will possibly be blocked by Barracuda unless I pay them $20 a year.
Sounds like Blackmail to me.
I also note that although EmailReg.org appears to be a separate entity, it is in fact owned by Barracuda. So a neutral third party blocking service just so happens to be owned by the people doing the blocking. If thats not a conflict of interest, I don’t know what is!
This is actually illegal in some countries, although apparently, not the USA.
It also doesn’t stop actual spammers coughing up money, and getting greenlisted.
Seems the rest of the net agrees with us on this one.
Quote from Mike E. that pretty much sums it up: I feel compelled to add this. If I’m paying Barracuda for a appliance to filter out spam and they in turn are being paid by spammers to allow their messages through my spam firewall, how is that different than an antivirus company taking money from somone that write viruses to have their product not detect a virus? None. It’s slimy.
So, in future when clients are unable to send mail to people using Barracuda firewall devices, I’ll be able to point them to this post, and let them know the situation.
We don’t like spam either, and work hard to avoid clients misusing our services.
However, we don’t blackmail senders into paying us money to accept their mail.
For a rundown on legitimate practices, read this:
http://en.wikipedia.org/wiki/Anti-spam_techniques_(e-mail)
Further References/Complaints:
http://www.nabble.com/zen.spamhaus.org-td22805806.html
http://www.debian-administration.org/users/simonw/weblog/295
http://zacharyozer.blogspot.com/2008/10/worst-engineers-ever.html
http://andrew.triumf.ca/barracuda-problems.html
http://community.spiceworks.com/topic/32502
http://steve.heyvan.com/2008/11/06/technology-reviews/barracudacentral-another-blacklist-black-hole/
http://ithelp.ithome.com.tw/question/10013491?tab=opinion (Trad Chinese)
http://www.linux.com/feature/155880
Archives
- November 2024
- November 2019
- October 2019
- August 2019
- April 2019
- February 2017
- September 2016
- June 2016
- May 2016
- September 2015
- August 2015
- June 2015
- April 2015
- December 2014
- October 2014
- September 2014
- July 2014
- June 2014
- April 2014
- October 2013
- July 2013
- May 2013
- April 2013
- March 2013
- January 2013
- December 2012
- October 2012
- August 2012
- July 2012
- June 2012
- May 2012
- April 2012
- March 2012
- December 2011
- November 2011
- October 2011
- September 2011
- July 2011
- May 2011
- April 2011
- March 2011
- February 2011
- January 2011
- December 2010
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
- May 2010
- April 2010
- March 2010
- February 2010
- January 2010
- December 2009
- November 2009
- October 2009
- May 2009
- April 2009
- March 2009
- February 2009
- January 2009
- December 2008
- November 2008
- October 2008
- September 2008
Categories
- Apple
- Arcade Machines
- Badges
- BMW
- China Related
- Cool Hunting
- Exploits
- Firmware
- Food
- General Talk
- government
- IP Cam
- iPhone
- Lasers
- legislation
- MODx
- MySQL
- notice
- qmail
- requirements
- Reviews
- Service Issues
- Tao Bao
- Technical Mumbo Jumbo
- Things that will get me censored
- Travel
- Uncategorized
- Useful Info